How Security Tags Work | There's only one way to shift security left and succeed against overwhelming technical debt: Putting developers front and center for application security. For more tips, including how to remove a security tag using rubber bands or pliers, read. The magnetic removers work with the magnetic locking tags and will never work with the clam tags. They can even be used with large hard tags.
Want to tell us how much you love us? Life hacks on security sensor tag how to remove! Some tags will also ruin a garment by spilling ink from the tag if you try to remove it yourself. Intro designed by joseph hung outro designed by jason. The magnetic removers work with the magnetic locking tags and will never work with the clam tags.
Finally, lift the pin out of its hole and remove the tag from your item of clothing. The magnetic security tag remover removes the pin from the tags and is specially designed to be mounted on top with the pos system or the counter. You might want to try putting the garment in the freezer to solidify the ink before attempting. This method will not work with ink tags; The magnetic removers work with the magnetic locking tags and will never work with the clam tags. Ink security tags consist of two pieces held together by a narrow pin. And what if removing the tag damages the product? How do shop security tags work? How do security tags work? Today, let's see how to remove security tags from clothes or other items in case they accidentally left them on in the shop. Security tags are labels which can be associated with a virtual machine (vm). Let's also see how do they work. The amount of information stored on an rfid tag varies.
There's only one way to shift security left and succeed against overwhelming technical debt: I discuss the eas (electronic article surveillance) security tags used on clothes and other high theft items as well as some of the tools to remove them. Seven questions to ask before using open source software at work. Cite me in your answer: How do shop security tags work?

Security tags are labels which can be associated with a virtual machine (vm). I'm not able to make it work… jsf 1.2 & spring 3.1, security 3.1 & webflow 2.3 library… every sec tags are ignored or not found. The magnetic chips at the gate of the shopping mart sense this device and make loud sound if the device comes in the magnetic field. Seven questions to ask before using open source software at work. The uniwiki will be undergoing maintenance on the weekend of march 21st, 2021. Some tags will also ruin a garment by spilling ink from the tag if you try to remove it yourself. I discuss the eas (electronic article surveillance) security tags used on clothes and other high theft items as well as some of the tools to remove them. Security clothing security guard clothing security clothing uniform security labels for clothing clothing ··· model number ks ip8 tag size diameter 10mm frequency 5.8khz/8.2mhz q factor ≥70 deactivation fieldstrength 0.9a/m—1.5a/m. This deactivator works by breaking a circuit within a label. Mibils security tag & labels are of the highest levels of security, they can be custom printed with custom text and variable data saying barcode,serial number. Related searches for how do clothing security tags work: Putting developers front and center for application security. The magnetic security tag remover removes the pin from the tags and is specially designed to be mounted on top with the pos system or the counter.
Some tags will also ruin a garment by spilling ink from the tag if you try to remove it yourself. You can view security tags applied on a virtual machine or create a user defined security tag. Security labels are usually deactivated by a deactivator that is situated at the point of sale or integrated into the scanner. Rather than this being a stressful issue, make it easy with these simple tips on how to remove those tags. Security clothing security guard clothing security clothing uniform security labels for clothing clothing ··· model number ks ip8 tag size diameter 10mm frequency 5.8khz/8.2mhz q factor ≥70 deactivation fieldstrength 0.9a/m—1.5a/m.
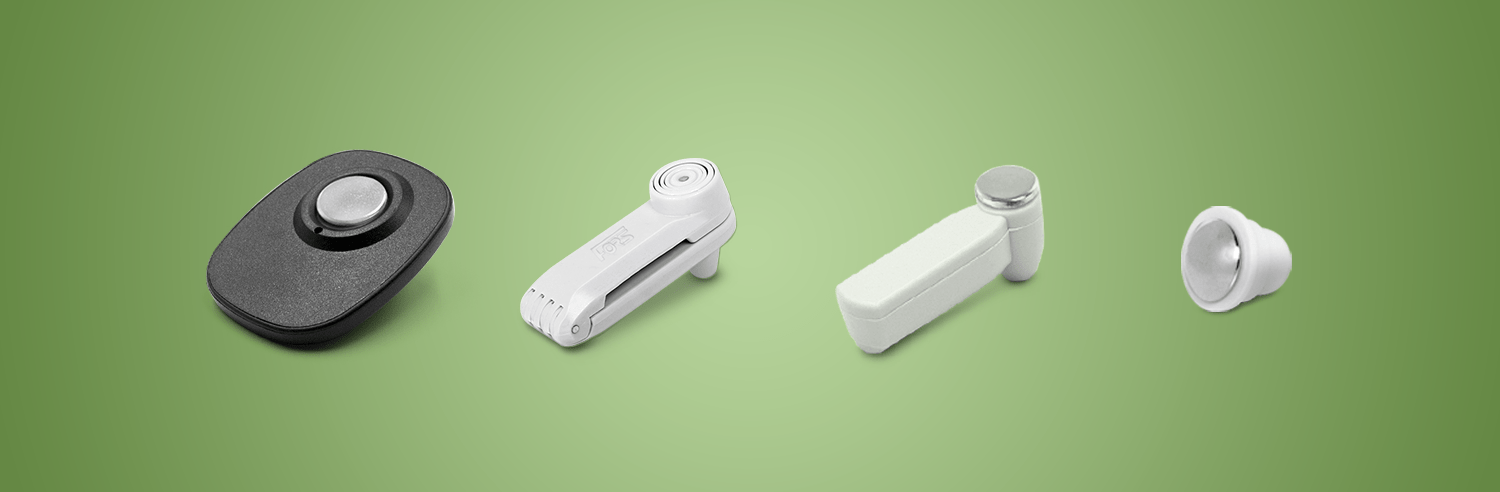
You are mixing spring security jsp tag with thymeleaf. How do security tags work? A basic rfid system comprises two parts: The above security tags are only available for jsp pages. How do security tags work? Today, let's see how to remove security tags from clothes or other items in case they accidentally left them on in the shop. I'm not able to make it work… jsf 1.2 & spring 3.1, security 3.1 & webflow 2.3 library… every sec tags are ignored or not found. Seeing the security tag on clothing merchandise can be very frustrating as it adds another step to process your inventory. Shoot us a message and we'll get back to you. Some tags will also ruin a garment by spilling ink from the tag if you try to remove it yourself. Mibils security tag & labels are of the highest levels of security, they can be custom printed with custom text and variable data saying barcode,serial number. The magnetic removers work with the magnetic locking tags and will never work with the clam tags. The only way to get a tag off once the two pieces are secure is with a special removal device, which detaches the two.
How Security Tags Work: Rather than this being a stressful issue, make it easy with these simple tips on how to remove those tags.
0 comments:
Post a Comment